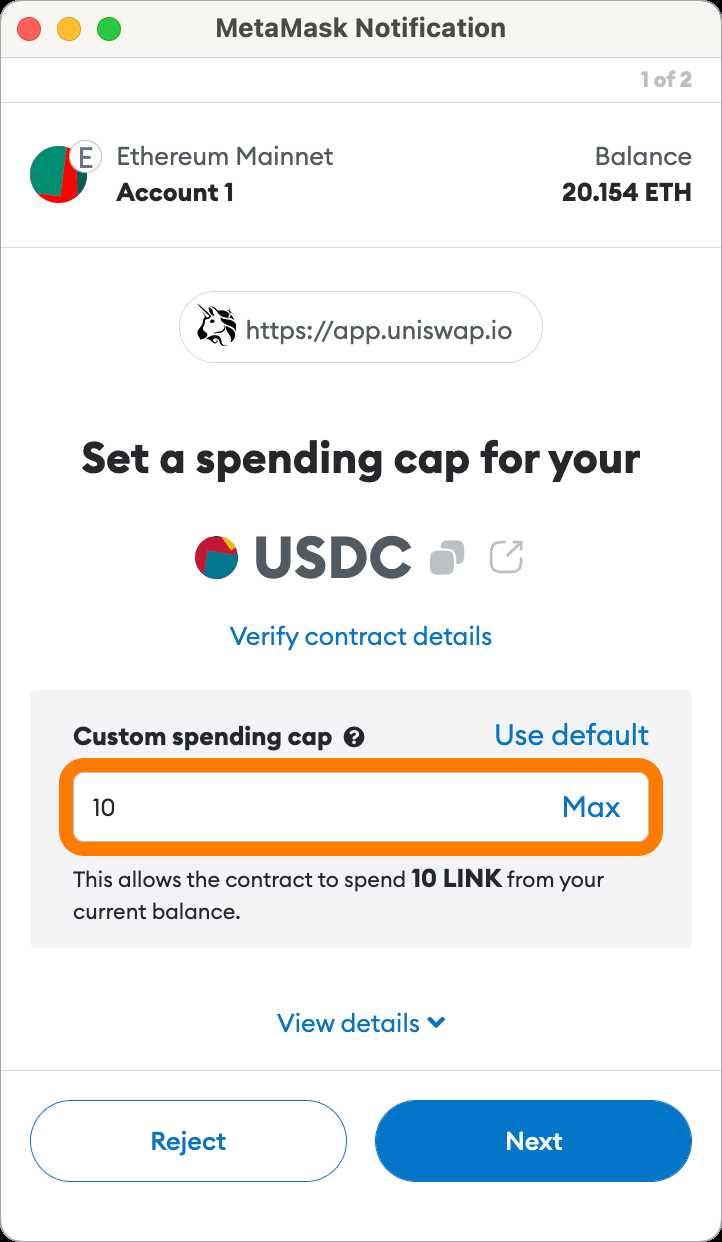
Metamask is one of the most popular digital wallet extensions for managing cryptocurrency assets on a web browser. It allows users to interact with decentralized applications (dApps) and securely store their Ethereum and ERC20 tokens. While Metamask offers a convenient and user-friendly experience, it is crucial to prioritize the security of your digital assets.
One essential security measure is to regularly review and revoke permissions granted to dApps. When you connect Metamask to a dApp, it requests specific permissions to interact with your wallet, such as the ability to transfer funds or access your account information. Revoking unnecessary permissions minimizes the risk of unauthorized access and potential loss of your digital assets.
To revoke permissions in Metamask, follow these simple steps. First, open your Metamask extension and click on the account icon in the top-right corner. From the drop-down menu, select “Settings.” In the Settings tab, navigate to the “Connections” section.
Under “Connections,” you will see a list of dApps that have been granted permission to access your Metamask wallet. Carefully review the list and identify any dApps that you no longer use or trust. To revoke permissions for a specific dApp, click on the three vertical dots next to its name and select “Revoke Permissions.” Confirm the action, and the dApp will no longer have access to your wallet.
Regularly reviewing and revoking permissions in Metamask is a crucial aspect of securing your digital assets. Be proactive in managing your wallet’s permissions to minimize the risk of unauthorized access and protect your valuable cryptocurrency holdings.
Understanding Digital Asset Security

In today’s digital age, protecting your digital assets is of utmost importance. From cryptocurrencies and NFTs to personal data and intellectual property, securing your digital assets should be a top priority.
The Importance of Digital Asset Security
Digital assets, such as cryptocurrencies like Bitcoin and Ethereum, are becoming increasingly valuable. It’s crucial to understand the risks involved and take necessary precautions to protect these assets from hackers and cyber threats.
When it comes to digital asset security, there are a few key points to keep in mind:
- Secure Storage: Storing your digital assets in a secure wallet or vault is essential. Hardware wallets, such as Trezor or Ledger, offer an extra layer of protection by keeping your private keys offline.
- Multiplying Protections: Implementing multiple layers of security, such as two-factor authentication (2FA) or biometric verification, adds an extra level of protection to your digital assets.
- Regular Updates and Backups: Keeping your software and wallets up to date ensures that you have the latest security patches. Additionally, regularly backing up your wallet ensures that you can recover your assets in case of loss or theft.
Securing Digital Assets with Metamask
Metamask is a popular cryptocurrency wallet that allows users to manage their digital assets and interact with decentralized applications (dApps) on the Ethereum blockchain. Understanding how to secure your assets with Metamask is essential in protecting against unauthorized access.
Some security measures to consider when using Metamask include:
- Strong Password: Creating a strong, unique password for your Metamask wallet is crucial. Avoid using common passwords and consider using a password manager for added security.
- Backup Seed Phrase: Metamask provides a seed phrase during wallet creation. It is essential to write down and store this phrase in a safe place. This seed phrase can be used to restore your wallet if your device is lost or compromised.
- Permissions Management: Metamask allows you to grant permissions to dApps. It is important to review and revoke permissions regularly to ensure that only trusted applications have access to your assets.
By understanding the importance of digital asset security and taking necessary precautions, you can protect your valuable assets from unauthorized access and potential loss.
The Importance of Protecting Your Digital Assets

In the digital age, our valuable assets have transitioned from physical possessions to digital ones. From our personal information and financial records to our intellectual property and creative works, these digital assets are now more vulnerable than ever.
One of the most crucial steps in securing your digital assets is taking measures to protect them from unauthorized access and potential threats. By doing so, you can ensure the safety and integrity of your data, minimize the risk of identity theft, and prevent the loss or misuse of your assets.
1. Safeguarding Personal Information
Your personal information, such as social security numbers, addresses, and passwords, needs to be treated with the utmost care. Implementing strong passwords, using two-factor authentication, and regularly updating your login credentials are essential steps to protect your personal information from unauthorized access.
2. Securing Financial Records
In the digital world, our financial records are accessible through online banking platforms and mobile applications. It is vital to secure these platforms with strong passwords, regularly monitor your accounts for any suspicious activities, and only use secure and trusted networks when accessing your financial information.
Furthermore, consider using encryption methods and secure backup solutions to store your financial records in case of device theft or data loss.
3. Protecting Intellectual Property and Creative Works

As a creator, it is crucial to protect your intellectual property and creative works from unauthorized use or distribution. Registering your copyrights, trademarks, and patents provides legal protections that can help you enforce your rights and prevent infringement.
In addition to legal measures, using digital rights management (DRM) tools and watermarking your digital assets can deter unauthorized use and ensure proper attribution.
In conclusion, securing your digital assets is of utmost importance in today’s digital world. By taking proactive measures to protect your personal information, financial records, and intellectual property, you can safeguard your valuable assets and mitigate the risks associated with digital vulnerabilities.
Introducing Metamask

Metamask is a browser extension and mobile application that allows users to manage their digital assets, interact with decentralized applications (DApps), and securely store private keys on their device. It acts as a cryptocurrency wallet, giving users control over their digital assets and providing a convenient way to access the Ethereum blockchain.
With Metamask, users can easily create and manage multiple Ethereum accounts, view transaction history, and send or receive Ether and other ERC-20 tokens. It also acts as a bridge between the traditional web and the decentralized web, enabling seamless integration and interaction with various DApps.
One of the core features of Metamask is its ability to connect to multiple networks. By default, it is connected to the Ethereum Mainnet, but users can easily switch to other networks like the Ropsten Testnet or their own local blockchain. This flexibility allows developers to test their DApps on different networks and enables users to access a wide variety of DApps and blockchain applications.
Metamask prioritizes user security and privacy. It uses various encryption techniques to protect private keys and sensitive information. Users are also required to set up a password and create a unique seed phrase during the initial setup process. This seed phrase can be used to restore access to the wallet and recover funds in case of device loss or failure.
Furthermore, Metamask provides users with the ability to revoke permissions granted to DApps. This means that users have full control over which DApps can access their digital assets and personal information. Revoking permissions is an essential security measure, as it prevents malicious or untrustworthy DApps from accessing and potentially compromising the user’s assets.
In conclusion, Metamask is a powerful tool that empowers users to securely manage their digital assets and interact with the decentralized web. Its intuitive interface, multiple network support, and emphasis on security make it a popular choice among Ethereum users and developers alike.
Overview of Metamask and Its Features
Metamask is a web browser extension that allows users to interact with the Ethereum blockchain. It acts as a bridge between users’ web browsers and the Ethereum network, enabling them to securely manage their digital assets and interact with decentralized applications (dApps).
Key Features of Metamask

- Wallet Management: Metamask provides users with a wallet for managing their Ethereum accounts. It allows users to create multiple accounts, import existing accounts, and securely store their private keys.
- Transaction Signing: With Metamask, users can sign transactions and send them to the Ethereum network. It provides a seamless and secure way to authorize transactions.
- Ethereum Network Connectivity: Metamask allows users to connect to different Ethereum networks, such as the mainnet, testnets, and custom networks. This flexibility enables users to test their dApps on different networks before deploying them to the mainnet.
- Interaction with dApps: Metamask makes it easy for users to interact with decentralized applications. It injects the necessary Ethereum provider into the web browser, allowing users to interact with dApps without the need for any additional software or hardware wallets.
- Secure Token Management: Metamask supports the management of various Ethereum-based tokens. Users can view their token balances, send and receive tokens, and even add custom tokens to their wallet.
- Smart Contract Execution: Metamask provides a user-friendly interface for interacting with smart contracts on the Ethereum network. Users can execute smart contract functions, view their transaction history, and monitor the status of their transactions.
- Privacy and Security: Metamask takes privacy and security seriously. It encrypts users’ private keys and stores them locally in their web browser. Metamask also supports hardware wallet integration for added security.
In conclusion, Metamask is a powerful tool for securely managing digital assets and interacting with the Ethereum blockchain. Its user-friendly interface and feature-rich functionality make it a popular choice among both beginners and experienced Ethereum users.
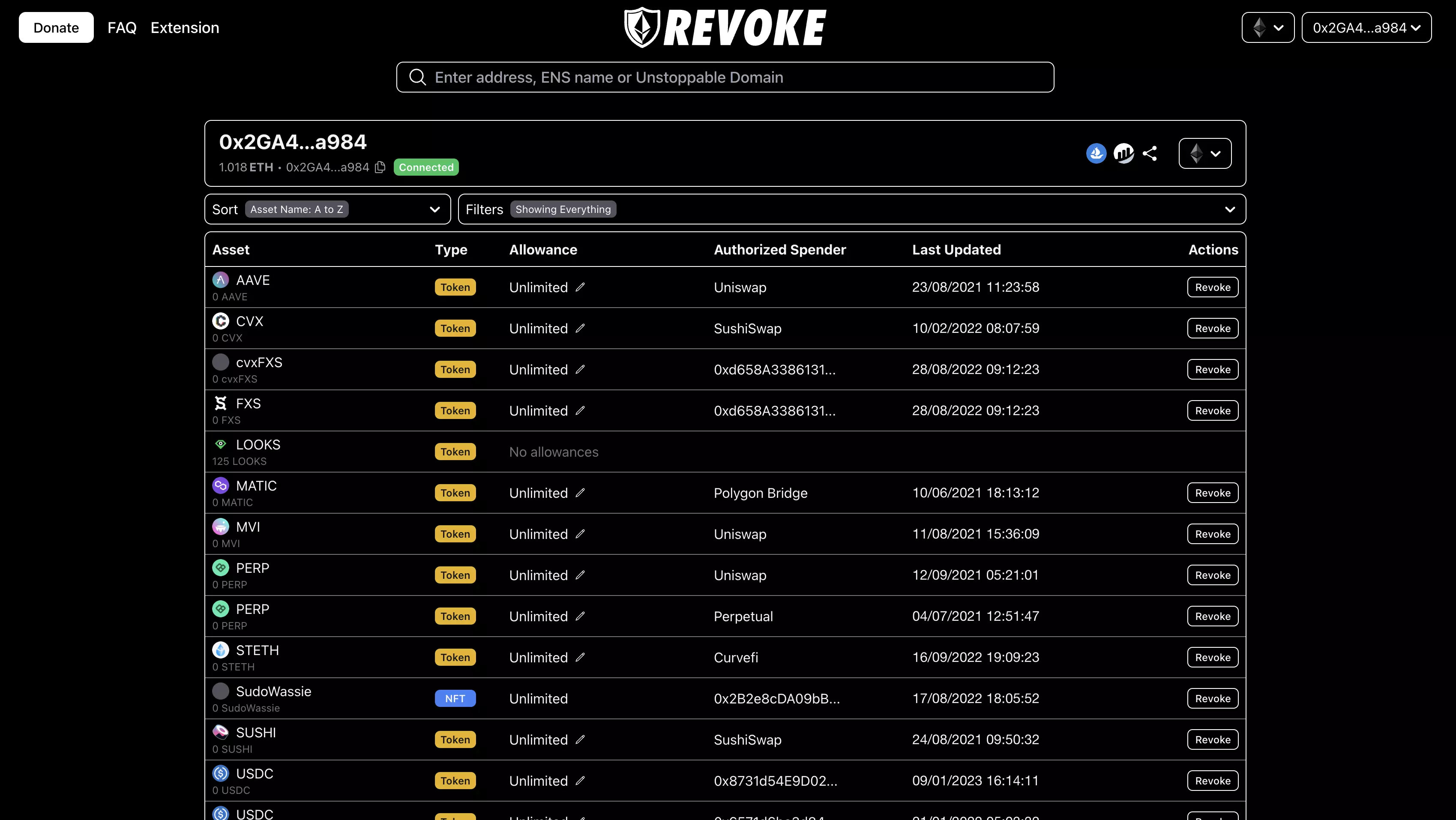
Revoking Permissions in Metamask
Metamask is a popular web extension and wallet for the Ethereum blockchain, allowing users to interact with decentralized applications (dApps) securely. While it provides a convenient way to manage digital assets, it is crucial to be mindful of the permissions granted to dApps.
Revoking permissions in Metamask is essential to ensure the security of your digital assets. By granting permissions, you allow the dApps to access specific account information, such as your wallet balance or the ability to send transactions on your behalf.
To revoke permissions in Metamask, follow these simple steps:
- Open your browser and click on the Metamask extension icon located in the top-right corner.
- A popup window will appear, displaying your current wallet balance and recent transactions.
- Click on the three horizontal lines icon to open the Metamask menu.
- In the menu, select “Settings.”
- Under the “Connections” section, you will find a list of connected dApps.
- To revoke permissions for a specific dApp, click on the “X” icon next to its name.
- A confirmation prompt will appear asking if you want to revoke permissions for that dApp. Click “Revoke” to confirm.
By following these steps, you can easily revoke permissions for any dApp that you no longer trust or wish to grant access to your account information. This helps minimize the risk of unauthorized access and potential loss of your valuable digital assets.
It is essential to review the permissions granted to dApps regularly and revoke access for any suspicious or unnecessary applications. By staying vigilant and taking control of your permissions in Metamask, you can enhance the security of your digital assets and protect yourself from potential threats.
Why Revoking Permissions is Crucial for Security
When it comes to securing your digital assets, revoking permissions should be at the top of your list. Whether you are using Metamask or any other digital wallet, giving permissions to third-party applications can expose you to various security risks.
Revoking permissions is crucial for security because:
- Protecting your funds: When you grant permissions to a third-party application, it gains access to your digital assets. If the application is compromised or malicious, it can drain your funds without your knowledge. By revoking permissions, you minimize the risk of unauthorized access to your assets.
- Preventing unauthorized actions: Some applications may request permission to execute actions on your behalf, such as making transactions or interacting with smart contracts. If you no longer trust the application or want to limit its capabilities, revoking permissions can prevent any unauthorized actions from being performed using your wallet.
- Minimizing data exposure: Granting permissions to applications often involves sharing sensitive information, such as your wallet address or private key. Revoking permissions ensures that these details are no longer accessible to the application, reducing the risk of data breaches or identity theft.
- Preventing phishing attacks: Phishing attacks are a common method used to deceive users into granting permissions to fake applications. By revoking permissions regularly, you can mitigate the risk of falling victim to these scams and protect your assets from being stolen.
- Maintaining control: Revoking permissions allows you to regain full control over your digital assets. It ensures that no third-party application has access or control over your funds, reducing the chances of any unwanted or unauthorized activities.
Ultimately, revoking permissions is essential to safeguarding your digital assets. By regularly reviewing and revoking permissions for applications you no longer use or trust, you can significantly improve the security of your funds and protect yourself from potential risks.
How does revoking permissions in Metamask help secure your digital assets?
Revoking permissions in Metamask can help secure your digital assets by ensuring that only authorized applications have access to your wallet. By revoking permissions, you can prevent malicious applications from making unauthorized transactions or accessing your private keys.
What steps are involved in revoking permissions in Metamask?
Revoking permissions in Metamask is a simple process. First, open the Metamask extension in your browser and click on the menu icon. Then, select “Settings” from the dropdown menu. In the Settings tab, scroll down to the “Connected Sites” section and click on “Connected sites”. Here, you will see a list of all the applications that have permission to access your wallet. To revoke permission for a specific application, click on the “X” icon next to its name. Confirm the revocation by clicking on the “Disconnect” button. Repeat this process for all the applications you want to revoke permissions from.
Can revoking permissions in Metamask prevent phishing attacks?
Revoking permissions in Metamask can help prevent phishing attacks to some extent. Phishing attacks often try to trick users into granting permission to malicious applications. By regularly checking the list of connected sites in Metamask and revoking permissions from unknown or suspicious applications, you can reduce the risk of falling victim to phishing attacks. However, it’s important to stay vigilant and follow other security best practices to fully protect yourself from phishing.