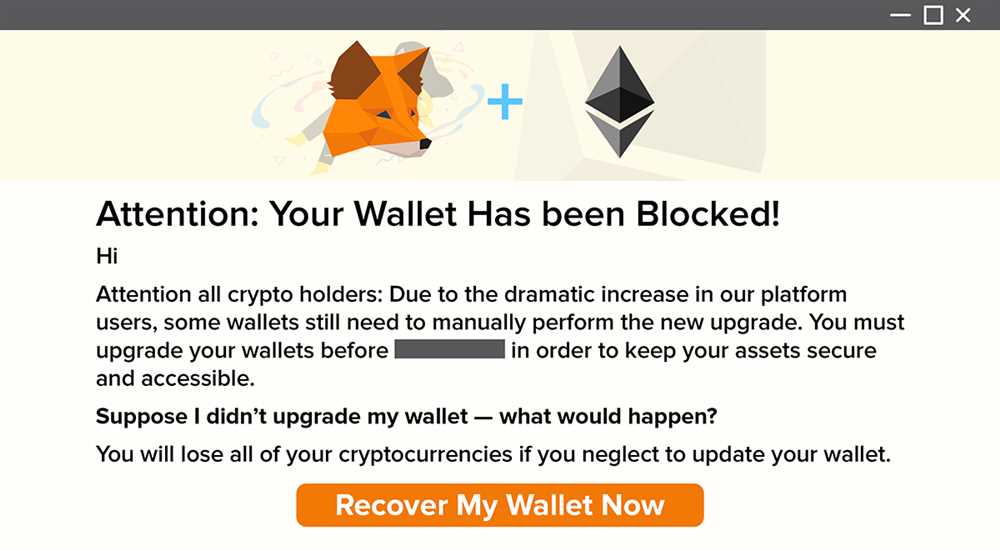
Metamask, the popular digital wallet for managing cryptocurrencies, has recently been targeted by spam emails. These emails, disguised as official communication from Metamask, aim to deceive users and steal their personal information. It is important to be aware of this phishing attempt and take necessary precautions to protect yourself.
What is a spam email?
Spam emails are unsolicited messages sent in bulk, often with malicious intent. They can contain links to fraudulent websites or attachments with malware. In the case of Metamask spam emails, the sender poses as a legitimate representative of Metamask and tries to trick recipients into revealing sensitive information such as passwords or private keys.
How to identify spam emails?
It is crucial to be able to distinguish between genuine emails and spam. Here are a few signs that can help you identify a Metamask spam email:
- The email address of the sender does not match the official Metamask domain.
- The email contains grammatical errors or typos.
- There is a sense of urgency in the email, pressuring you to take immediate action.
- The email asks for sensitive information, such as your password or private keys.
How to protect yourself?
To protect yourself from falling victim to Metamask spam emails, it is essential to follow these guidelines:
- Verify the sender’s email address. Double-check that it matches the official Metamask domain.
- Exercise caution when clicking on links or downloading attachments from unknown sources.
- Enable two-factor authentication for your Metamask account to add an extra layer of security.
- Keep your software and antivirus programs up to date to prevent malware infections.
By staying vigilant and taking necessary precautions, you can protect yourself from falling victim to Metamask spam emails and safeguard your valuable cryptocurrency assets.
What is Metamask
Metamask is a popular cryptocurrency wallet browser extension that allows users to interact with decentralized applications (DApps) on the Ethereum blockchain. It acts as a bridge between traditional web browsers and the Ethereum network, enabling users to securely manage their digital assets, sign transactions, and interact with smart contracts directly from their browser.
Metamask provides a user-friendly interface and simplifies the complicated processes involved in interacting with the Ethereum blockchain. It stores private keys and allows users to manage multiple accounts, import and export wallets, and securely store their digital assets.
With Metamask, users can seamlessly access various DApps without the need for separate wallets or installations. It acts as a digital identity and facilitates seamless authentication and authorization for transactions on the Ethereum network.
Key Features of Metamask:
- Ease of Use: Metamask provides a simple and intuitive interface, making it easy for beginners to navigate and interact with DApps.
- Security: Private keys are encrypted locally and never leave the user’s device, providing a secure way to manage digital assets.
- Compatibility: Metamask is compatible with major web browsers such as Chrome, Firefox, and Brave, allowing users to access DApps seamlessly.
- Multiple Networks: It supports multiple Ethereum networks, including the mainnet, testnets, and custom networks, enabling developers to test their DApps in different environments.
- Smart Contract Interaction: Metamask allows users to interact with smart contracts, execute transactions, and view transaction history directly from the browser.
How Metamask Works:
Metamask operates as a browser extension and injects a JavaScript library into the user’s browser. This library provides a set of APIs that allow developers to interact with the Ethereum network.
When a user visits a DApp, Metamask prompts them to authorize the connection and provides a secure interface to interact with the DApp. It handles all the complex cryptographic operations, such as signing transactions and verifying signatures, without exposing the user’s private keys.
Metamask also maintains a local cache of the Ethereum blockchain, known as the state. This allows users to access the blockchain quickly and reduces the reliance on external nodes.
In summary, Metamask is a powerful tool that brings together the convenience of web browsers and the functionality of the Ethereum blockchain, allowing users to securely manage their digital assets and interact with DApps seamlessly.
Metamask Spam Emails
Metamask is an increasingly popular browser extension and mobile app that allows users to interact with Ethereum-based decentralized applications (dApps) and manage their cryptocurrency wallets. With the rise of blockchain technology and the growing interest in decentralized finance (DeFi), the usage of Metamask has skyrocketed in recent years.
However, with popularity comes the risk of scams and phishing attempts. One common tactic used by cybercriminals is sending spam emails disguised as official Metamask communications, aiming to trick recipients into revealing their sensitive information or downloading malware.
It is important for Metamask users to be aware of these spam emails and to know how to identify and avoid them.
How to identify spam emails
Here are some red flags to look out for that may indicate an email is a spam:
- The sender’s email address does not match the official Metamask domain.
- The email contains poor grammar or spelling errors.
- The email asks for personal or financial information, such as passwords or private keys.
- The email includes suspicious attachments or links.
- The email creates a sense of urgency or uses scare tactics to prompt immediate action.
How to avoid falling for spam emails
To protect yourself from falling victim to spam emails, consider the following precautions:
- Always verify the sender’s email address before taking any action.
- Double-check the email for any signs of poor grammar or spelling mistakes.
- Do not share personal or financial information via email, especially passwords or private keys.
- Avoid clicking on suspicious attachments or links.
- If in doubt, contact Metamask support directly to verify the legitimacy of the email.
By staying vigilant and following these tips, you can help ensure the security of your Metamask wallet and protect yourself from falling victim to spam emails.
The Nature of the Emails
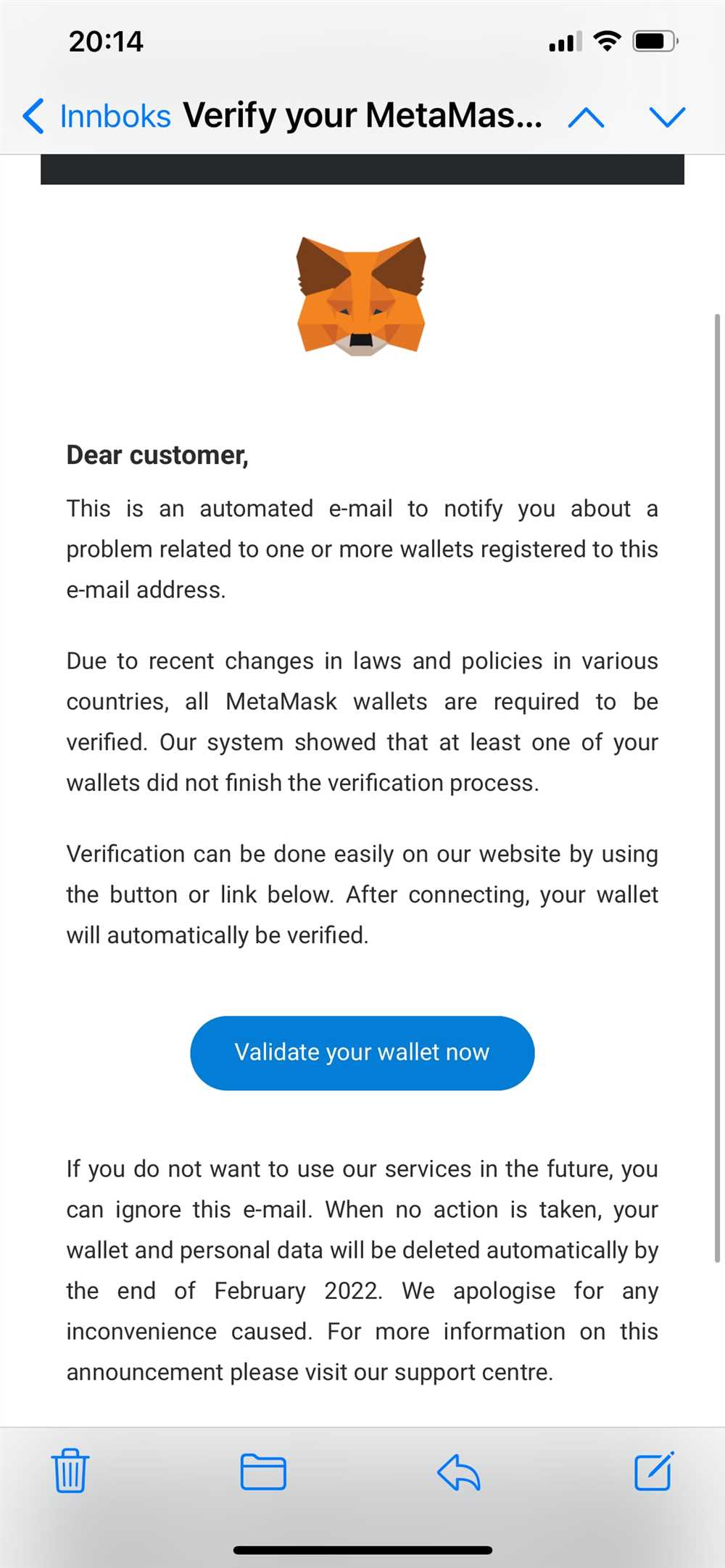
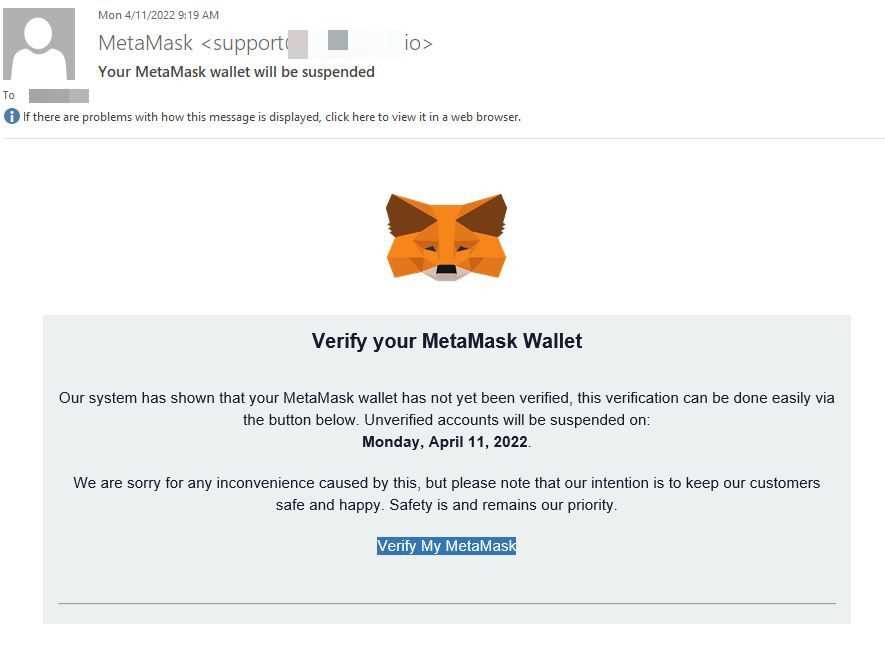
The emails claiming to be from Metamask are a form of spam designed to trick recipients into revealing sensitive information or installing malicious software. These emails often use scare tactics or urgent language to create a sense of urgency, leading users to make hasty and uninformed decisions.
It’s important to note that Metamask, as a reputable cryptocurrency wallet provider, will never send unsolicited emails requesting personal or financial information. Legitimate communications from Metamask will always come from official channels and will never ask for sensitive details via email.
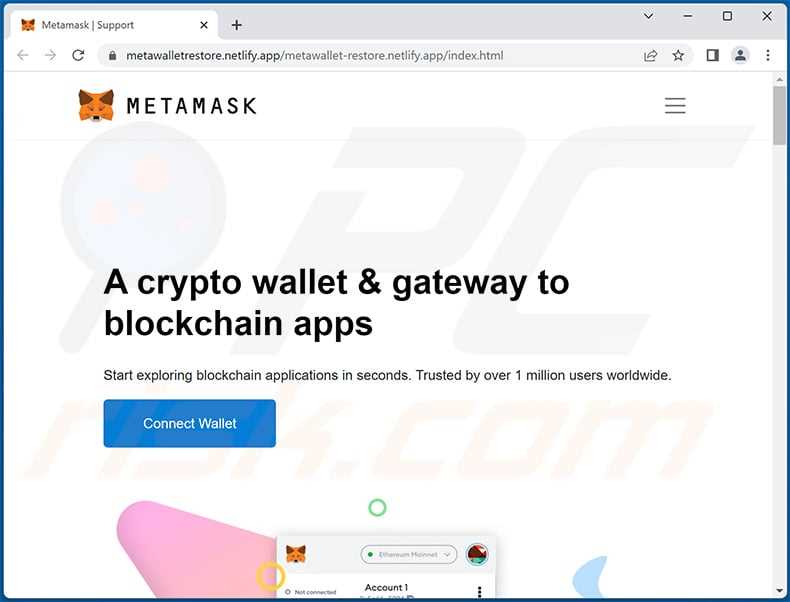
These spam emails may claim that there is an issue with the recipient’s Metamask account or that their funds are at risk. They may also request that the recipient download and install a fake version of the Metamask extension or provide their seed phrase or private key. These malicious actions can lead to the theft of funds or the compromise of personal information.
If you receive an email from an unknown or suspicious source claiming to be from Metamask, it is crucial to exercise caution and refrain from taking any actions suggested in the email. Instead, access your Metamask account directly through the official website or mobile app to ensure the security of your funds and personal information.
Always remember to stay vigilant and be wary of any unexpected or suspicious emails, especially those related to cryptocurrency wallets or financial accounts. By staying informed and using trusted sources of information, you can protect yourself from falling victim to scams and phishing attempts.
How to Identify and Avoid Spam Emails
With the increasing number of spam emails being sent each day, it’s important to know how to identify and avoid them. Here are some tips to help you stay safe:
1. Be wary of unknown senders
If you receive an email from someone you don’t recognize, exercise caution. Don’t automatically trust every email you receive, especially if it contains suspicious links or requests for personal information.
2. Watch out for phishing attempts
Phishing is a common method used by scammers to trick users into revealing their sensitive information. Look out for emails that ask for your passwords, credit card details, or social security numbers. Always verify the legitimacy of the sender before sharing any personal information.
3. Check for poor grammar and spelling
Spam emails often contain grammar and spelling mistakes. Legitimate companies usually have professional proofreaders, so if an email seems poorly written, it’s likely a spammy attempt.
4. Don’t click on suspicious links
Avoid clicking on links in emails that seem suspicious or unfamiliar. These links may lead you to phishing websites or download malicious software onto your device. Instead, manually type the website address into your browser to ensure you’re visiting a legitimate site.
5. Use a trusted spam filter
Utilize a reliable spam filter or email service that automatically detects and filters out spam emails. This can significantly reduce the number of unwanted messages that reach your inbox.
6. Update your email security settings
Regularly review and update your email account’s security settings. Enable two-factor authentication if available, and be sure to use a strong and unique password for your email account.
7. Be cautious of urgent or threatening language
Many spam emails use urgent or threatening language to manipulate recipients into taking action. If an email claims you must act immediately or face dire consequences, take a step back and consider its legitimacy before providing any information or clicking on any links.
By following these tips, you can better protect yourself from falling victim to spam emails. Stay vigilant and always prioritize your online security.
Impact of Metamask Spam Emails

Metamask spam emails can have significant consequences for users who fall victim to them. These emails are designed to trick users into revealing their private keys or other sensitive information, which can then be used by attackers to gain unauthorized access to their cryptocurrency wallets.
One of the primary impacts of falling for a Metamask spam email is the loss of funds. If a user unwittingly shares their private keys or other credentials with the attacker, they can quickly drain the funds from their wallet. This can result in the loss of not only the initial investment but also any potential profits or gains that the user may have accumulated.
Furthermore, falling for a Metamask spam email can also lead to identity theft. The attacker can use the stolen information to impersonate the user and carry out fraudulent activities in their name. This can have a lasting impact on the victim, affecting their financial security and reputation.
Phishing Attacks
Metamask spam emails often employ phishing techniques to deceive users. Phishing attacks are designed to appear as legitimate messages from reputable sources, such as Metamask or other popular cryptocurrency platforms. The emails may contain convincing logos, graphics, and language, making it difficult for users to identify them as malicious.
These phishing emails typically include a call to action, urging the user to click on a link or download an attachment. However, these links and attachments can lead to the installation of malware or the redirection to malicious websites. Once on these sites, users may unwittingly enter their private keys or other sensitive information, falling directly into the hands of attackers.
Protecting Yourself
To protect yourself from Metamask spam emails, it is essential to exercise caution and follow best security practices. Here are some steps you can take:
- Be vigilant: Pay attention to the details of the email, such as the sender’s email address and any grammatical errors or typos. Genuine emails from Metamask or other legitimate sources are unlikely to contain such mistakes.
- Verify the source: Before clicking on any links or downloading attachments, verify the authenticity of the email. Check for official communication channels, such as the official website or social media accounts, and contact support if necessary.
- Keep your software updated: Ensure that you are using the latest version of Metamask and have installed reputable antivirus and antimalware software. Regularly update these programs to protect against emerging threats.
- Use hardware wallets: Consider using hardware wallets for added security. These physical devices store your private keys offline, making them less susceptible to phishing attacks.
By staying alert and following these precautions, you can minimize the risk of falling victim to Metamask spam emails and protect your funds and personal information.
| Impact | Consequences |
|---|---|
| Loss of Funds | Attackers can drain the user’s wallet by gaining unauthorized access. |
| Identity Theft | Stolen information can be used to impersonate the user and carry out fraudulent activities. |
Financial and Security Risks
The Metamask spam emails not only pose a threat to your personal information and privacy, but they also carry significant financial and security risks. It is crucial to understand these risks and take appropriate measures to protect yourself.
1. Financial Risks
One of the major financial risks associated with spam emails is the possibility of falling victim to phishing scams. Phishing scams are designed to trick individuals into revealing sensitive financial information, such as credit card numbers, passwords, or bank account details. The scammers can then use this information to steal your money or identity.
In the case of Metamask, the spam emails often attempt to deceive users into entering their wallet credentials on fake websites. If you unknowingly provide your private keys or seed phrases to these malicious actors, they can gain unauthorized access to your cryptocurrency wallet and steal your funds.
2. Security Risks
Alongside the financial risks, spam emails can also pose significant security threats. Opening suspicious email attachments or clicking on malicious links can expose your device to malware, viruses, or other forms of malicious software. These threats can compromise the security of your device and allow hackers to gain unauthorized access to your personal data.
Moreover, interacting with spam emails can increase the likelihood of future spam and phishing attempts. When you engage with these emails, it signals to the spammers that your email address is active and responsive. This can lead to an influx of spam emails in your inbox and put you at a higher risk of falling victim to fraudulent schemes.
It is crucial to stay vigilant and take proactive measures to protect yourself from financial and security risks associated with Metamask spam emails. Avoid clicking on suspicious links or providing any personal information without verifying the legitimacy of the email. Install reputable antivirus software and keep it up to date to safeguard your device from malware and viruses.
Remember, your financial and personal security should always be a top priority! If you receive any suspicious emails claiming to be from Metamask, it’s best to report them and delete them immediately.
Damage to Reputation
Receiving spam emails not only poses a direct threat to your personal information and funds but also has the potential to damage your reputation.
When you receive unsolicited emails from scammers or phishing attempts through Metamask, it can create a negative perception of your online presence. If these emails contain malicious links or attachments, unknowingly opening them can compromise your security and put your reputation at risk.
For individuals, falling victim to scams can lead to embarrassment, as scammers may use your compromised account to send spam emails to your contacts or engage in fraudulent activities under your name. This can damage your relationships with friends, family, and colleagues who may unknowingly trust the content of these emails.
For businesses, spam emails can be even more detrimental to reputation. If scammers gain access to an employee’s Metamask wallet and use it to send spam emails, customers and partners may receive these messages, which can raise concerns about the security and trustworthiness of the company’s online operations.
The damage to reputation caused by spam emails can be long-lasting and hard to repair. It is essential to take action to protect yourself and your organization from falling victim to such scams.
Mitigating the Risk
To mitigate the risk of damage to your reputation from spam emails, it is important to:
- Enable spam filters and email security features provided by your email provider.
- Avoid opening emails or clicking on links from unknown or suspicious senders.
- Regularly update your Metamask software and ensure it is secured with a strong password and two-factor authentication.
- Be cautious when sharing personal or financial information online, especially through email.
Taking proactive measures can significantly reduce the likelihood of falling victim to spam emails and protect your reputation from being tarnished by scammers and fraudsters. By staying vigilant and informed, you can maintain a positive online presence and protect yourself and your organization from potential harm.
What are Metamask spam emails?
Metamask spam emails are unsolicited and unwanted emails that are sent to Metamask users. These emails often contain phishing attempts, scams, or malware in an attempt to steal personal information or gain unauthorized access to the user’s Metamask wallet.
How can I identify a Metamask spam email?
There are several signs that can help you identify a Metamask spam email. Look out for emails asking for your private keys, seed phrases, or any other personal information. Be cautious of emails with suspicious or unfamiliar senders, poor grammar or spelling mistakes, urgent requests, or emails that ask you to click on unfamiliar links or download files.
What should I do if I receive a Metamask spam email?
If you receive a Metamask spam email, it is important to not click on any links or download any files. Do not reply to the email or provide any personal information. Instead, report the email as spam to your email provider and delete it immediately. You can also contact the Metamask support team to inform them about the spam email.
How can I protect myself from Metamask spam emails?
To protect yourself from Metamask spam emails, it is important to be cautious and vigilant. Be wary of emails asking for personal information or requesting access to your Metamask wallet. Never share your private keys or seed phrases with anyone. Keep your Metamask software and antivirus programs updated, and regularly check for any suspicious activity or unknown transactions in your wallet.